Information Assurance Vulnerability Alert Database
Open Source Vulnerability Database. National Vulnerability Database NVD Launched by the National Institute of Standards and Technology NIST in 2005 NVD provides a vulnerability database of enhanced CVE content that is fully synchronized with the CVE List so any updates to CVE appear immediately in NVD.

Database Database What Is Database Data Data Mining What Is Sql What Is Data Database Definition Data Defin Relational Database Database Management System Dbms
Information Assurance Vulnerability Management IAVM is the process of the getting the IAVAs out to all Combatant.
Information assurance vulnerability alert database. Agencies and organizations that must report to US Cyber Command USCYBERCOM must be able to identify vulnerabilities identified by the Information Assurance Vulnerability Management IAVM Notices. Arcadyan-based routers and modems vulnerable to authentication bypass. An information assurance vulnerability alert IAVA is an announcement of a computer application software or operating system vulnerability notification in the form of alerts bulletins and technical advisories identified by DoD CERT a division of the US.
Published July 20 2021 Updated October 07 2021. These selected vulnerabilities are the mandated baseline or minimum configuration of all hosts residing on the GIG. Information assurance vulnerability alert are technical advisories alerts and vulnerabilities of applications operating systems and servers i dentified by DoD Computer Emergency Response Team which is a division of the United States Cyber Command.
An information assurance vulnerability alert IAVA. Information Assurance Vulnerability Alert. Information assurance vulnerability alert IAVA Notification that is generated when an Information Assurance vulnerability may result in an immediate and potentially severe threat to DoD systems and information.
Ensuring that there are no security vulnerabilities that would put a system at risk for attacks. Information Assurance Vulnerability Alert Policy Memorandum. IAVM Notices are published at several levels with differing priority categories.
This report provides a detailed list of the vulnerabilities identified from 2002 2015. Information Assurance Vulnerability Management. Which stated that information assurance is an essential element of operational readiness.
Information Assurance Vulnerability Alert Iranian Anti - Vivisection Association Iraq and Afghanistan Veterans of America defined vulnerability in CNSS Instruction No. Assessing information assurance vulnerabilities. The combatant commands services agencies and field activities are required to implement vulnerability notifications in the form of alerts bulletins and technical advisories.
You can also report a vulnerability to us with or without a VINCE account. An information assurance vulnerability alert IAVA is an announcement of a comp. Information assurance vulnerability management IAVM program.
Factor Analysis of Information Risk Fair information practice Information Assurance Vulnerability Alert Information security ISO IEC 27001 ISO 9001 ISO 17799 IAVA may refer to. CVE IDs are mapped to the US Defense Information System Agencys Information Assurance Vulnerability Alerts IAVAs downloads of which are posted on DISAs public Security Technical Implementation Guides STIG websiteIAVA the DISA-based vulnerability mapping database is based on existing SCAP sources and once in a while it contains details for government systems that. If you are a vendor and would like to communicate with us about a vulnerability or update your contact information please create an account or sign in.
Information Assurance Vulnerability Management IAVM Last Updated On March 22 2019. An information assurance vulnerability alert IAVA is an announcement of a computer application software or operating system vulnerability notification in the form of alerts bulletins and technical advisories identified by DoD-CERT a division of the United States Cyber CommandThese selected vulnerabilities are the mandated baseline or minimum configuration of all hosts residing on the GIG. I need this for a security purpose.
Providing Internetwork Operating System updates for JNN-Ns routers and performing version upgrades to make sure software is not outdated. Information Assurance Vulnerability Alert IAVA. On December 30 1999 the Deputy Secretary of Defense issued an Information Assurance Vulnerability Alert IAVA policy memorandum requiring all the Commanders in Chief CINC the Services and Defense agencies CSA to.
4009 dated 26 April 2010 National Information. Develop a cross functional technical physical personnel and environmental matrix team consisting of empowered management and staff who are tasked to develop and manage long-term strategic direction for the organization Information Assurance Program incorporating. Information Assurance Vulnerability Alert - Background Background On February 15 1998 the Deputy Secretary of Defense issued a classified memorandum on Information Assurance that instructed the DISA with the assistance of the Military Departments to develop an alert system that ensured positive control of information assurance.
In terms of the JNN-N post-deployment software support and post-production software support includes Information Assurance Vulnerability Alert releases. World Heritage Encyclopedia the aggregation of the largest online encyclopedias available and the most definitive collection ever assembled. Network intrusion prevention and detection system IDSIPS Nessus Nessus Vulnerability Scanner.
On December 30 1999 the Deputy Secretary of Defense issued a memorandum Department of Defense DoD Information Assurance Vulnerability Alert IA. Welcome to the CERTCC Vulnerability Information and Coordination Environment VINCE. This alert requires corrective action because of the severity of the vulnerability risk.
The policy memorandum instructs the DISA to develop and maintain an IAVA database system that would ensure a positive control mechanism for system administrators to receive acknowledge and comply with system vulnerability alert notifications. IIS Security feature bypass vulnerability - CVE-2014-4078 MS14-076 Description. Information Assurance Vulnerability Alerts IAVA is a database containting known vulnerabilites gathered by the STIG Security technical Implementation Guide of Public Cyber Exchange.
I couldnt find the IAVA database website or the procedure to obtain it. The IP Security feature in Microsoft Internet Information Services IIS 80 and 85 does not properly process wildcard allow and deny rules for domains within the IP Address and Domain Restrictions list which makes it easier for remote attackers to. NVD also provides advanced searching a CVSS calculator for CVE IDs and fix information for CVE IDs.

Vulnerability Information An Overview Sciencedirect Topics

Roles Of Three Lines Of Defense For Information Security And Governance
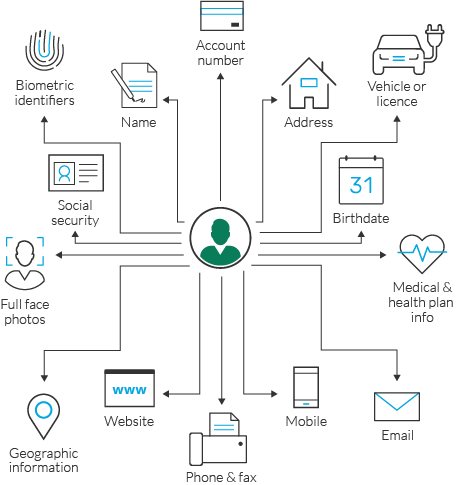
What Is Personally Identifiable Information Pii Data Security Imperva
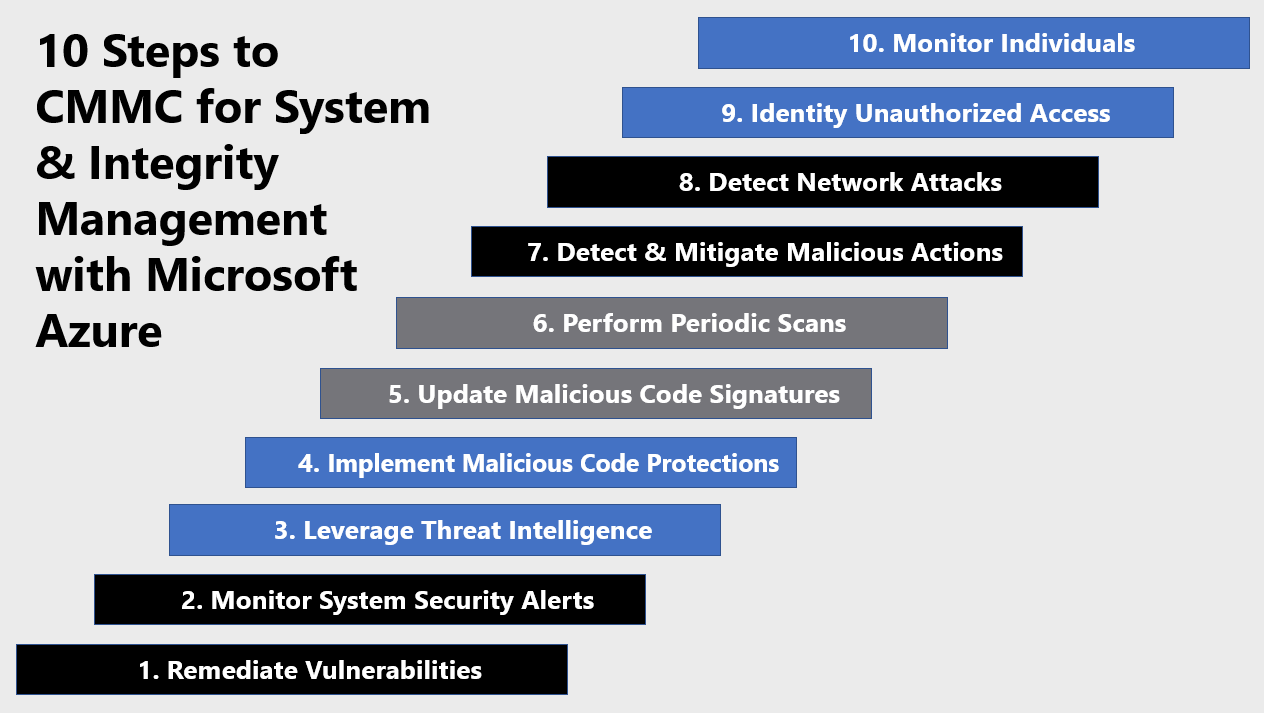
Cmmc With Microsoft Azure System Information Integrity 10 Of 10 Azure Government
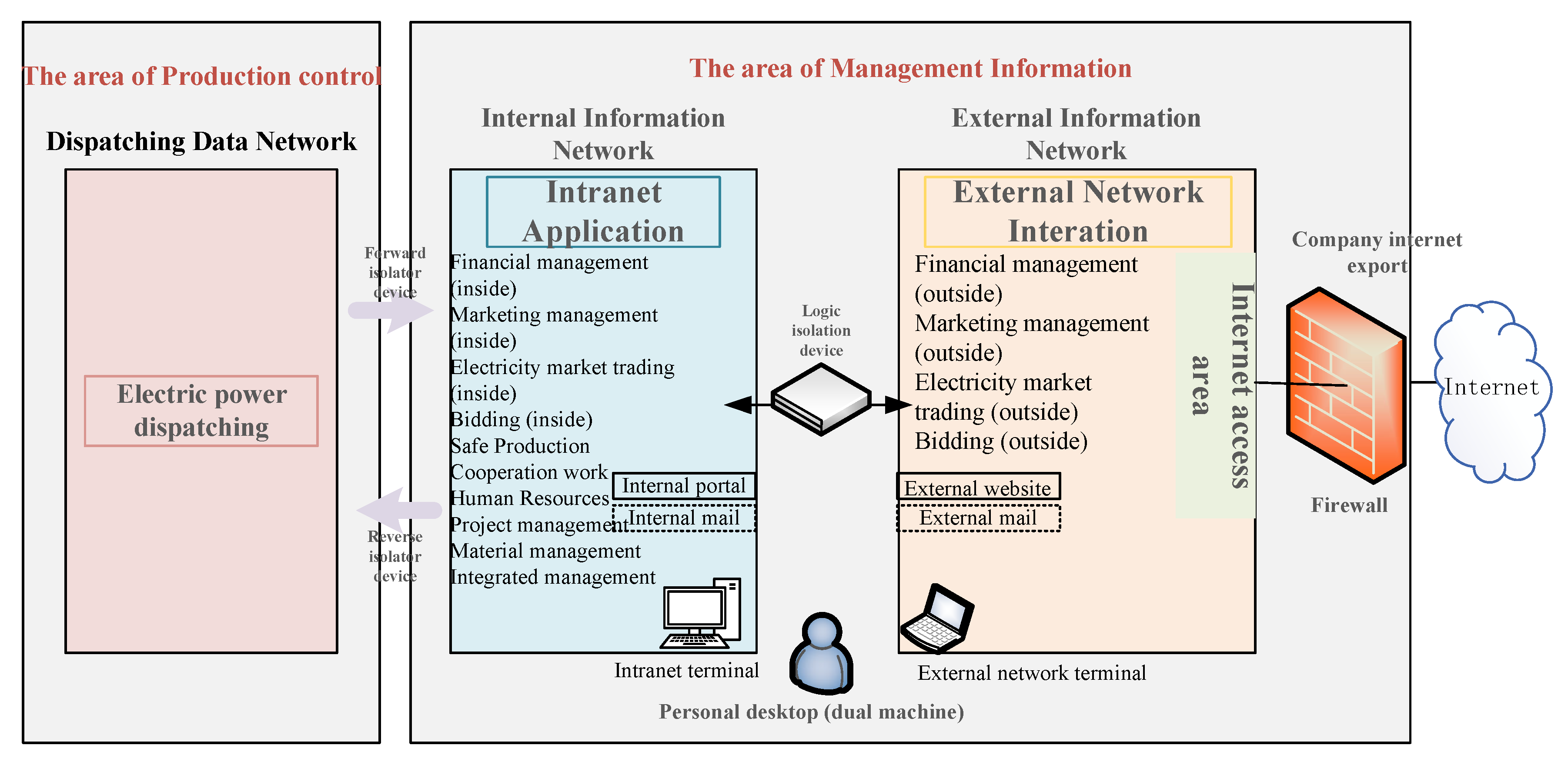
Information Free Full Text Information Security Risk Propagation Model Based On The Seir Infectious Disease Model For Smart Grid Html

Comprehensive Guide On Medusa A Brute Forcing Tool Medusa Electronics Projects Cyber Security
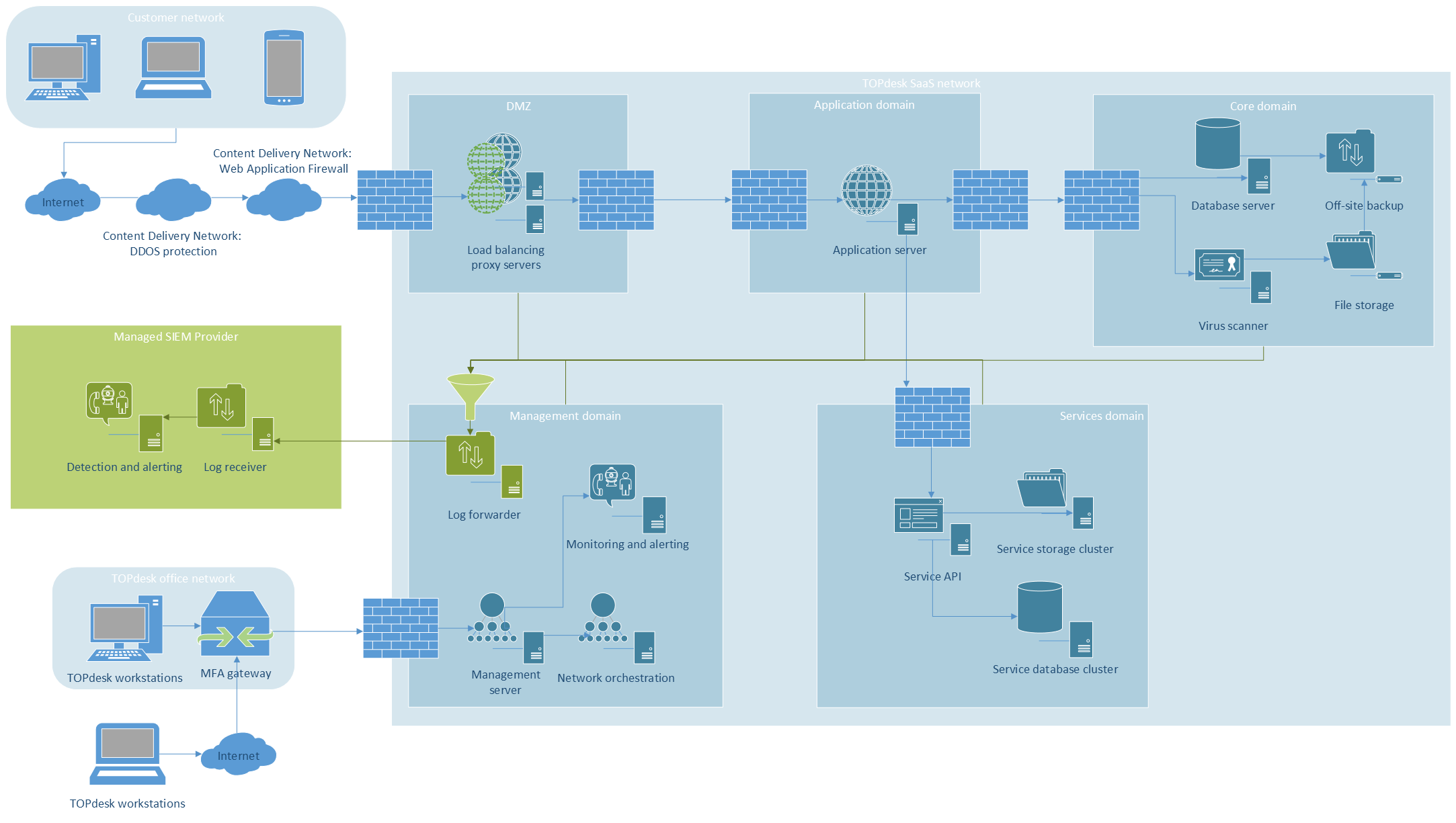
Saas Information Topdesk Software And Consultancy
What Is Information Securtiy Policy Principles Threats Imperva
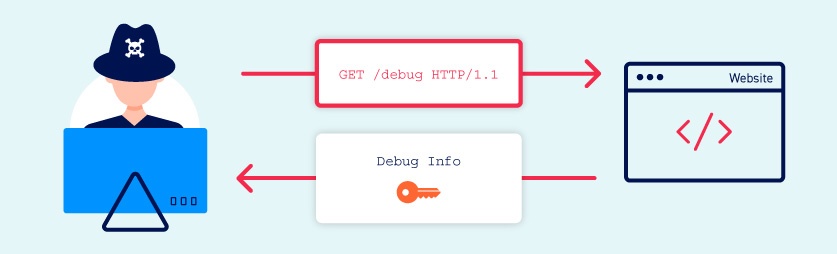
Information Disclosure Vulnerabilities Web Security Academy

Azure Sql Advanced Data Security Data Discovery Classification
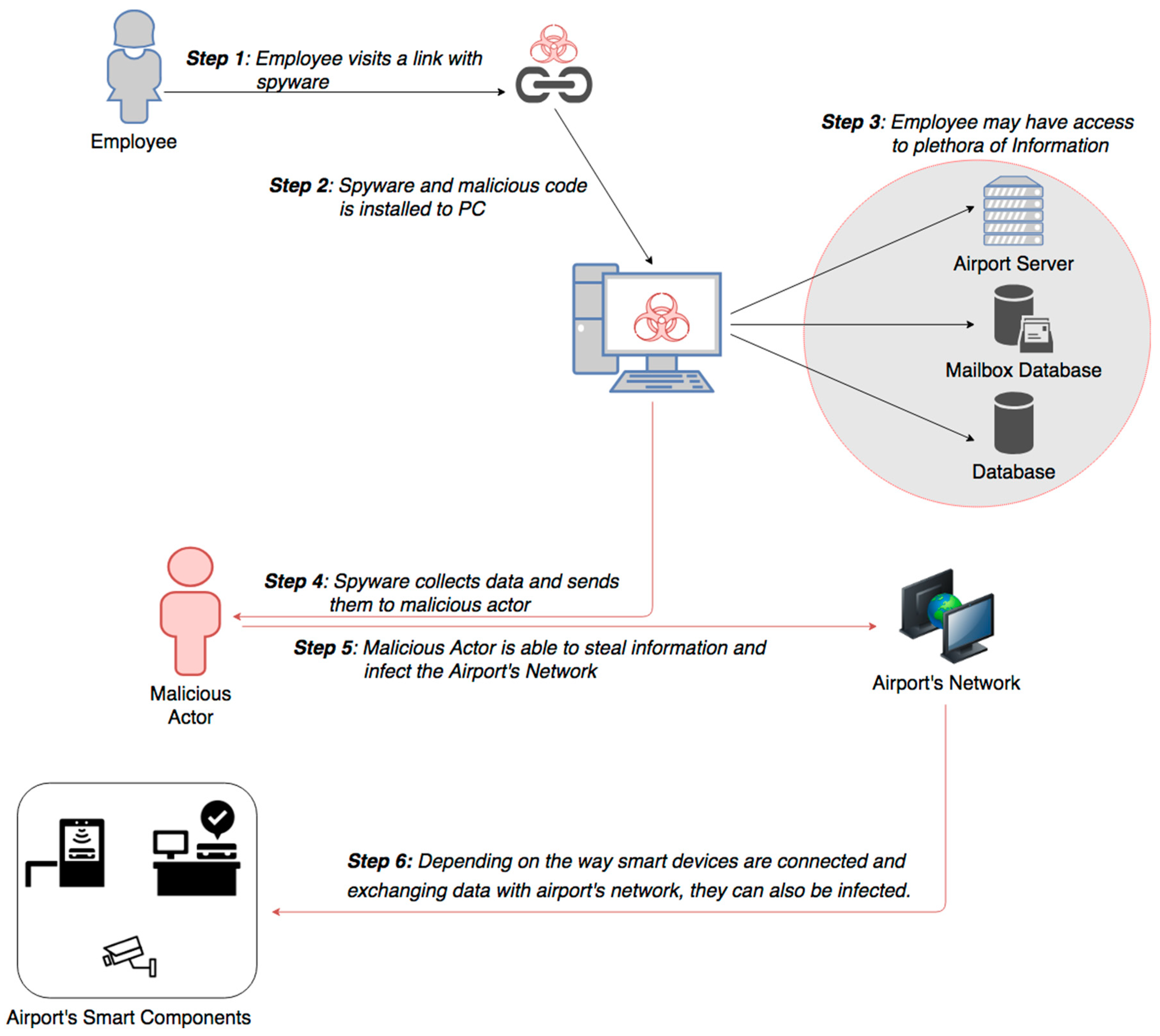
Sensors Free Full Text Smart Airport Cybersecurity Threat Mitigation And Cyber Resilience Controls Html
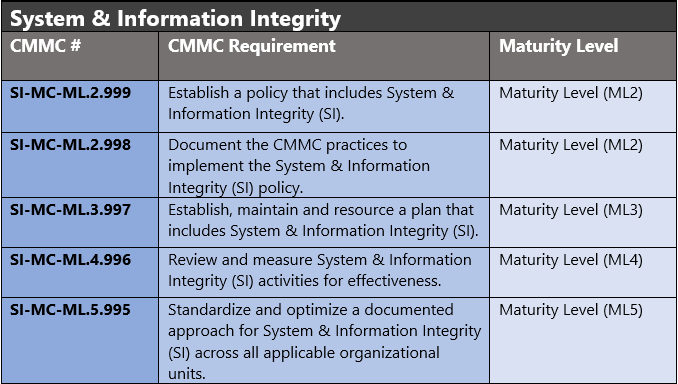
Cmmc With Microsoft Azure System Information Integrity 10 Of 10 Azure Government
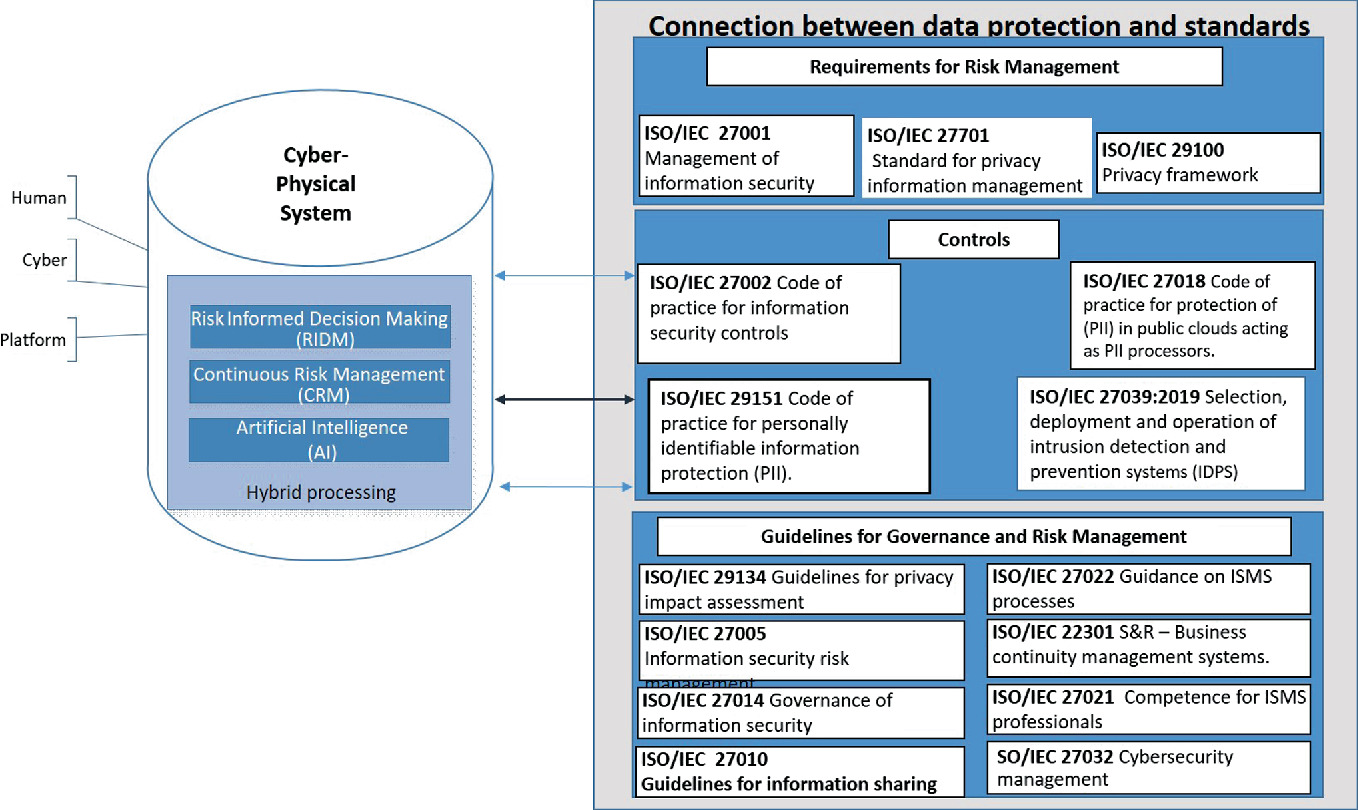
Comparing Cybersecurity Information Exchange Models And Standards For The Common Secure Information Management Framework Springerlink
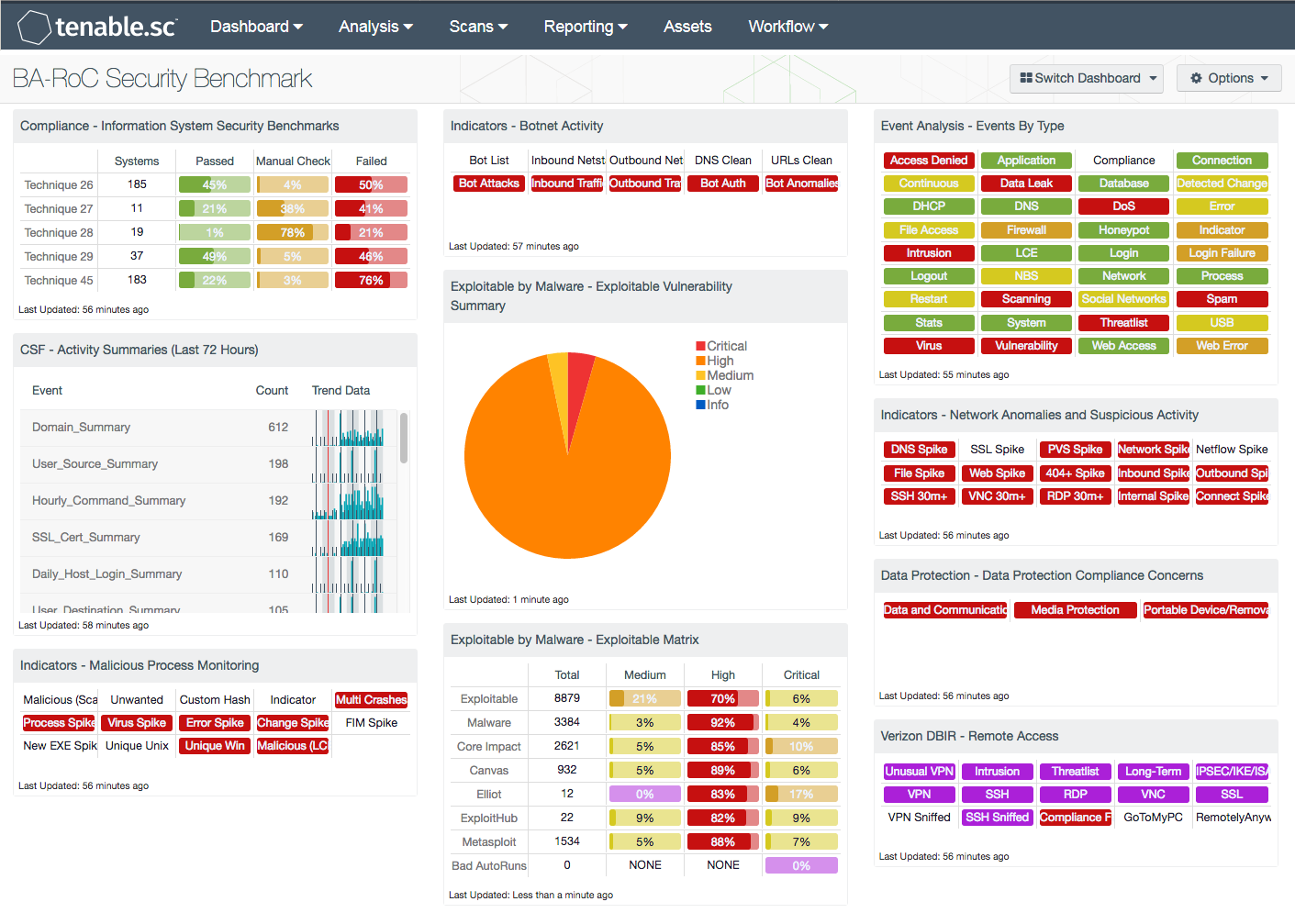
Ba Roc Information System Security Benchmark And Usage Sc Dashboard Tenable
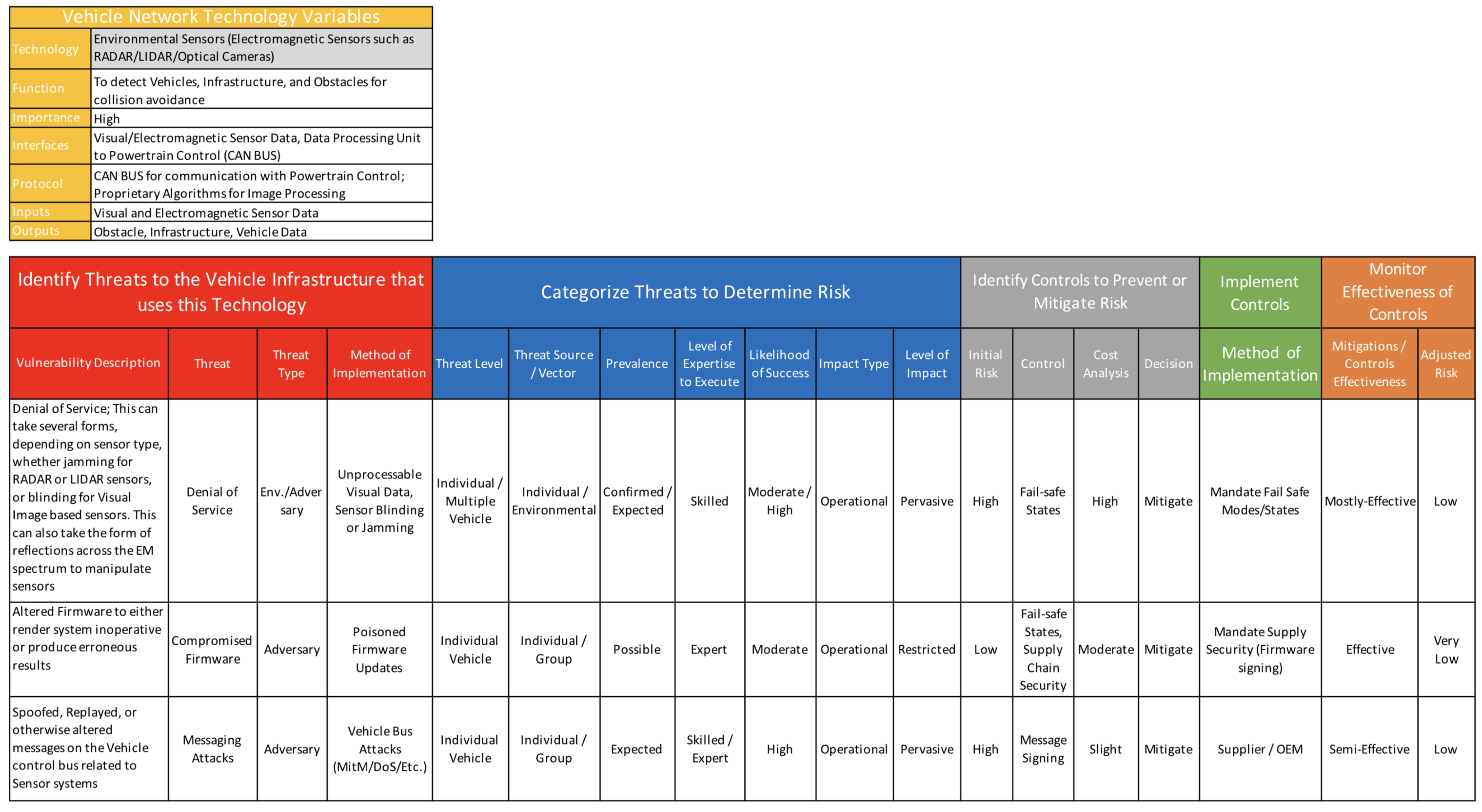
Information Free Full Text Leveraging Aviation Risk Models To Combat Cybersecurity Threats In Vehicular Networks Html

Cybersecurity Isn T The Same Thing As Information Assurance Cyber Security Security Definitions

Microsoft Defender Atp Integrates With Microsoft Information Protection To Discover Protect And Monitor Sensitive Data On Windows Devices Microsoft Security Blog
Posting Komentar untuk "Information Assurance Vulnerability Alert Database"